What can I do to help combat cyber attacks?
Cyber attacks are now part of our business environment and we have to accept and protect our businesses from attacks as best we can. We can no longer ignore this threat to our businesses. The National Cyber Security Centre have created a useful start framework to help you work through how to reduce the impact to your business from a successful cyber attack.
If you do suffer a cyber attack MJD have direct links to The Cyber and Fraud Centre Scotland, and importantly through this centre to Police Scotland and the Banks, this enables us to get rapid action to report the cyber attack and if money has been defrauded get action by the Police and the banks.
There are some cost effective and recommended methods to help reduce your exposure to cyber attacks which are outlined in Cyber Essentials such as firewalls, virus and malware protection, patch management, secure configuration, password policies and how user permissions are setup. Further steps you can take are security monitoring, training of your users to ensure their awareness of the threats to the business and incident management. Further reading on the steps to introduce Cyber Security to your business can be found at the following two links:
https://www.ncsc.gov.uk/collection/10-steps
https://www.ncsc.gov.uk/collection/small-business-guide
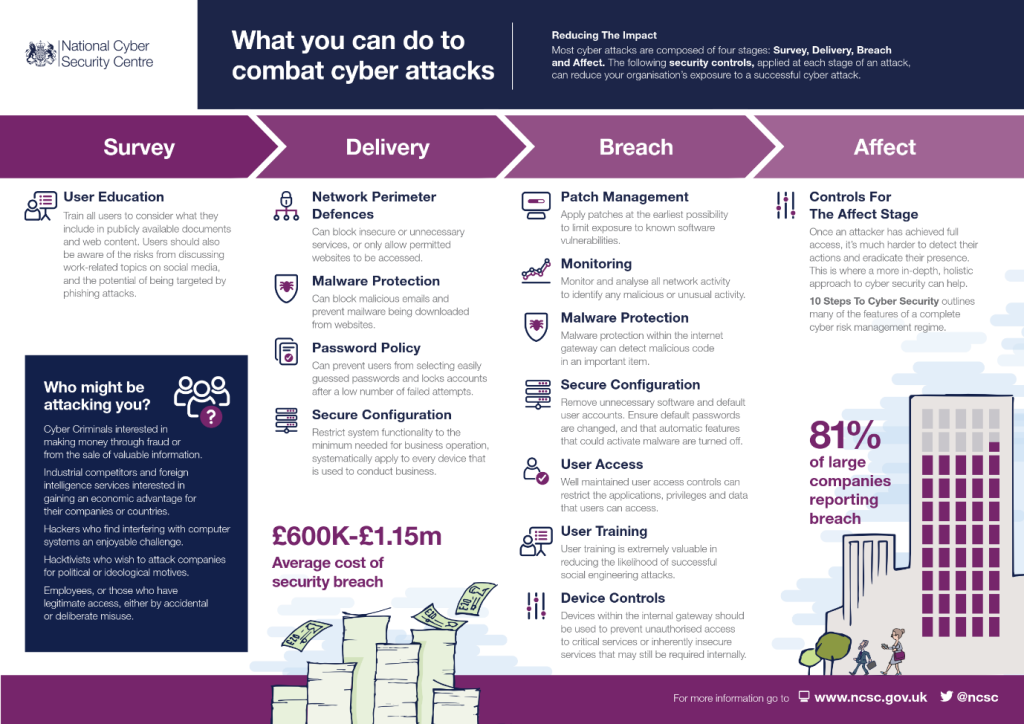
Lets go through the steps outlined in the NCSC’s infographic below. As a business you want to mitigate the survey stage. This is the stage where social engineering is taking place by the potential attackers, they gather as much information as they can on their potential targets through information publicly available and trying to gain information from your employees. This is why user training, education and awareness is so important in your cyber security defences in today’s environment. If you are unsure what social engineering is we covered this in a past blog post here (https://www.mjdsystems.co.uk/521-2/) It is also important to ensure employees think about the company information they make publicly available in published documents and on social media.
Here at MJD we have a recommended training system that will send fake phishing emails to users in the business which helps to keep the threat in your employees minds and provide training there and then if they don’t identify the potential risk and click on a link in the email. This takes the hassle out of organising and keeping training up to date for your employees and ensures they are regularly made aware of the threat.
Antivirus software is not enough! There are various processes and products that you can use to mitigate the delivery stage. This is when the attackers try to carry out the actual attack to gain access to your systems. The options available to the attackers can be reduced through the employment of anti-virus and malware protection, firewalls, password policies and secure configuration of permissions to users and devices.
The next stage is the part we all don’t want to get to, but we must plan and prepare for if the eventuality happens to us, and that is the breach stage. Do you have a disaster recovery plan if the worst happens? Ways to mitigate this stage is effective patch management, anti-virus and malware protection, consistently well-implemented and maintained user access controls and user training and awareness.
We have an industry recommended and leading anti-virus and malware protection software which we recommended and use for our clients. This software also provides us with remote monitoring and patch management to ensure our clients devices are kept up to date to reduce the risk of known vulnerabilities being exploited.
When we get to the affect stage it can be harder to detect the activities of the attacker, as if all the previous recommendations at each stage are implemented it has been a targeted and bespoke attack to gain entry. However, here at MJD we have a few systems we can utilize to monitor activity in our clients systems and spot unusual activity. If you have any questions on this area, we’d encourage you to get in touch to discuss with us as this area requires a more tailored approach to your specific organisation.
https://www.ncsc.gov.uk/guidance/white-papers/common-cyber-attacks-reducing-impact