Gone Phishing!
Today we want to talk about phishing emails. A phishing email is an email which has been sent to the recipient with the purpose of convincing you to provide them with your personal information or account details. Once they have this information they may use it to create accounts in your name or to gain access to steal more of your sensitive data. Reports conducted for this year by Webroot show us that there has been a 640% increase in phishing URLs being sent. This highlights the importance of being aware of how to protect yourself from phishing campaigns. The key to protecting yourself against phishing attacks is a continuous training programme. Statistics in this report also show that after 1 year of training, end users are 70% less likely to click through to a phishing attempt. The team at MJD can help to setup email training campaigns to help combat phishing attacks, so if after readying this article and encouraging your colleagues and peers to read this blog article you would like more training please just get in touch.
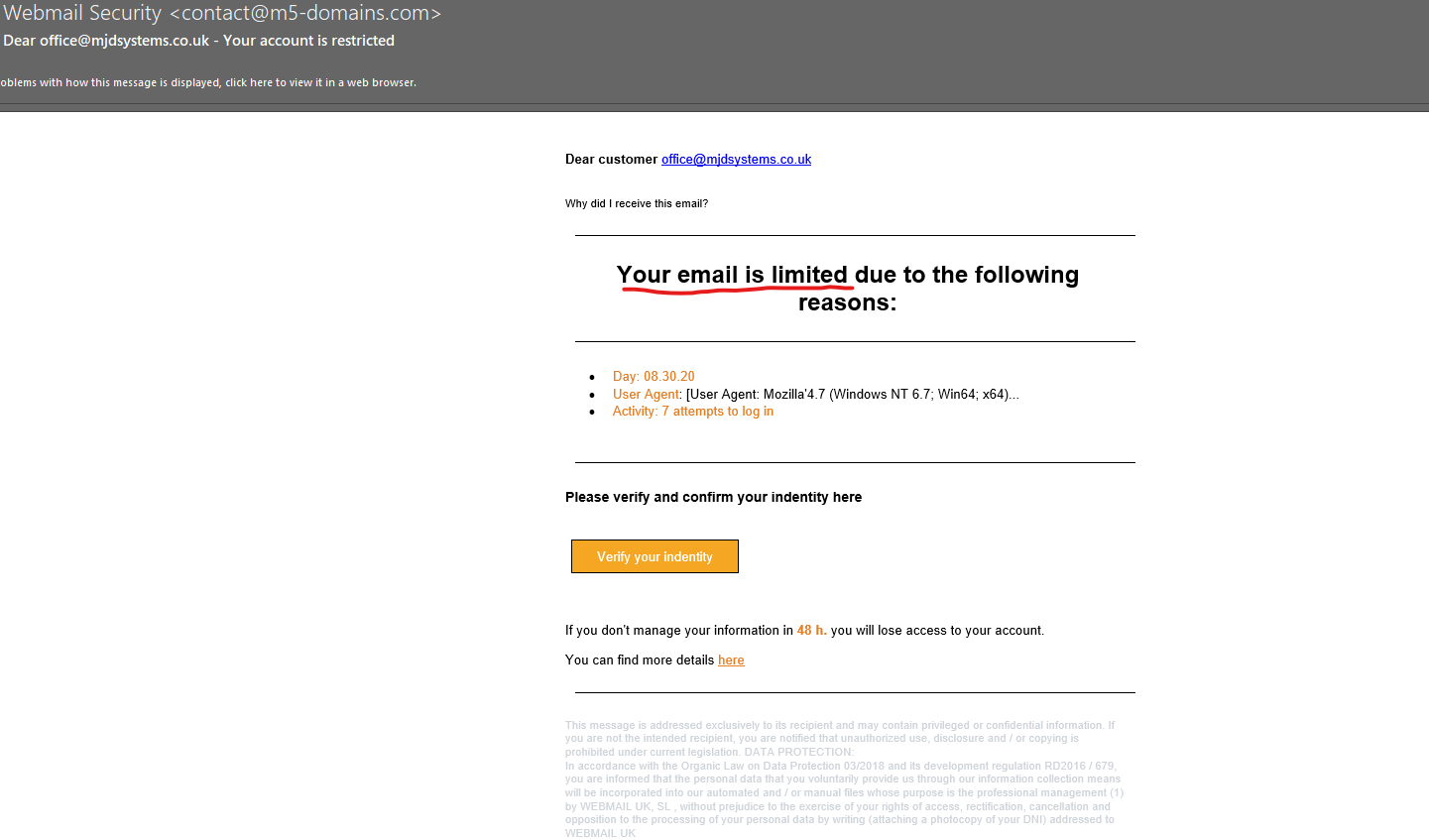
The key to remember is that most legitimate companies you conduct business or personal dealings with will not request sensitive information from you via email. However, the cyber criminals behind the phishing emails are getting ever cleverer and more careful about the look and feel of their emails, making our daily job of determining genuine emails from dangerous more difficult in our already hectic work lives. For this reason, we are going to dissect and exam a phishing email we recently received ourselves, to help you to understand the various warning signs and parts of an email to check before interacting with the information contain in the message in anyway.
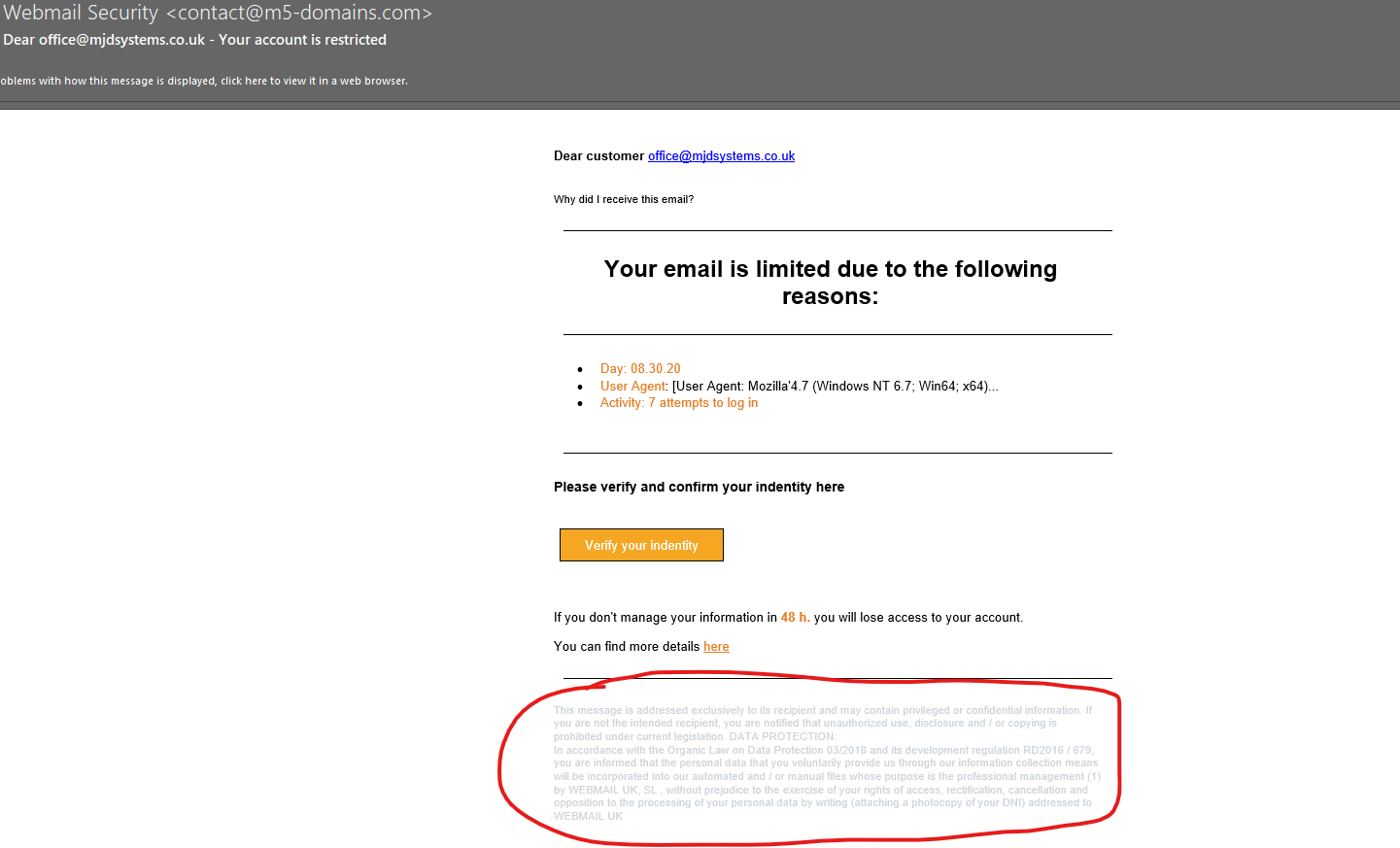
The first point of call is to consider the supposed reason for receiving the email. In this example, we are being told our email is limited. So take a moment, and think am I experiencing an issue like this.
We currently don’t have any issues with this email account being limited, so already alarm bells are ringing.
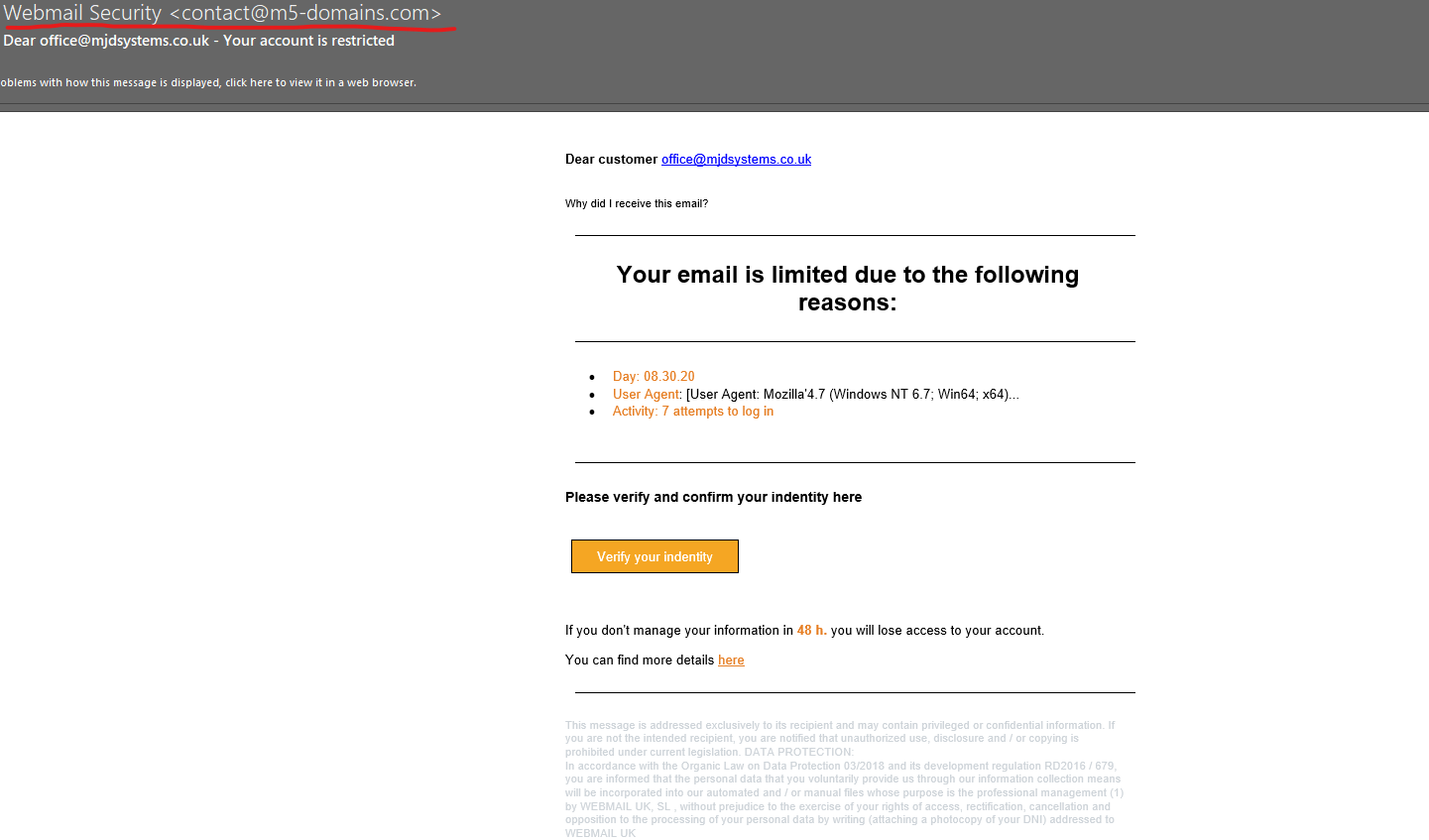
Next, we consider who the email is coming from. In this instance its coming from “Webmail Security”.
We don’t use webmail, so already this would not be someone we would expect to get messages about email issues from. On top of that, the actual email address of @m5-domains.com is not a company we have our domain with, therefore again we would not expect them to know anything about any email problems. So question do you interact with this company and use this company’s services? Therefore, should they be getting in touch with you?
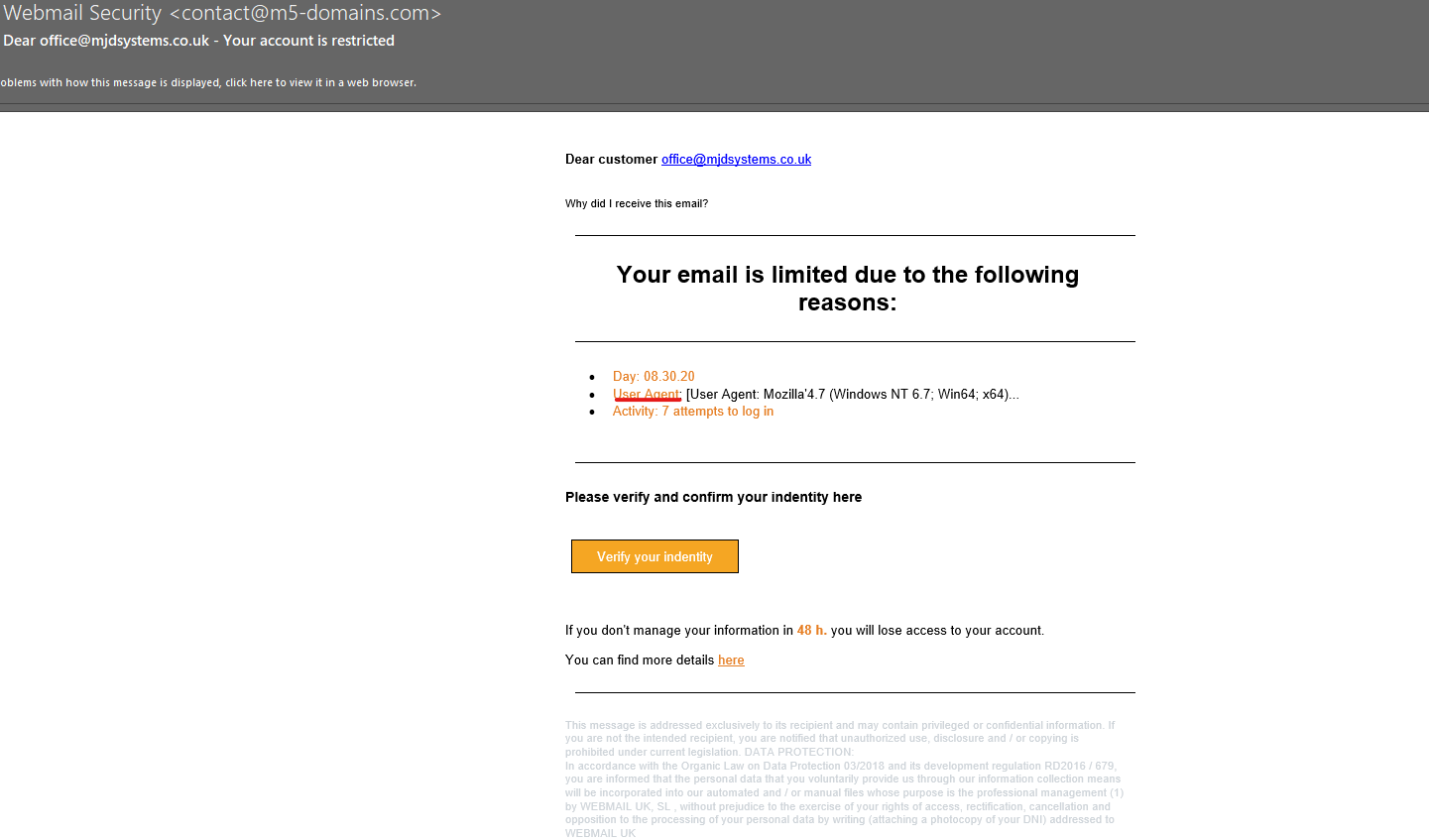
Within the body of the message you can see they use a term User Agent, which is like a fingerprint when you may have logged into a website or service through an Internet Browser. It takes details of the browser you used to access the service or webpage. Now, for a MSP we know what this is and straight away know we haven’t tried to log into our emails using these browsers. However, this specialist terminology is used to try and confuse the recipient in the hopes they don’t know what it is. This is another tactic all working towards encouraging you to act on the email and click their link.
At this point, we have already decided that this is a phishing email, but for the purpose of our blog post we will continue to question the remaining aspects of the email. For the cyber criminal who has sent this email, the next part is the most important part of their email, the link to their web page.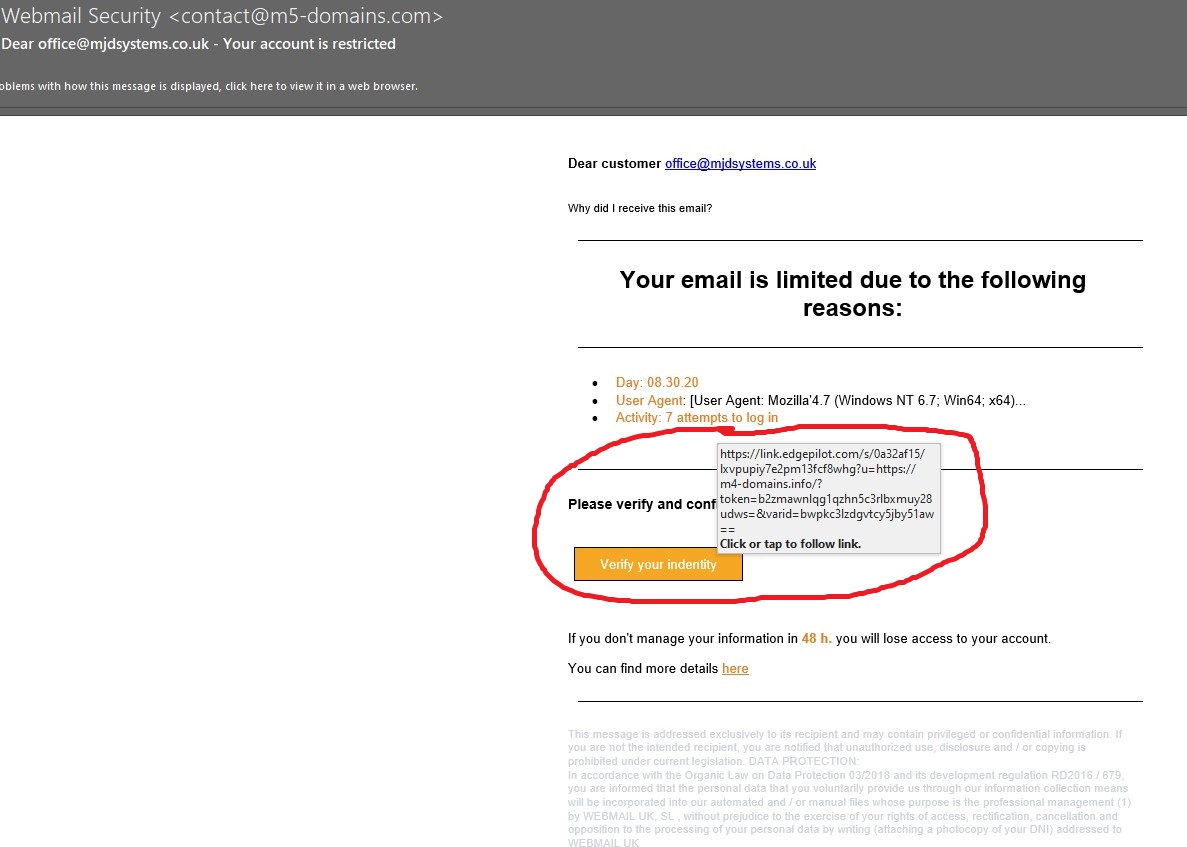
When we hover over the link you can see the URL which this button would take you too. In this case it lists a web page that has a different domain name, m4 domains rather than m5 domains, to the email address sending the email. Another red flag. Most likely this would lead you to a web page where it would ask for your username and password to “verify your identity”. These would then be stored in a database and used to try and gain access to your account. It is key that you should remember to NEVER enter your credentials anywhere other than when genuinely gaining access to your emails and you should NEVER share your credentials with anyone.
What you will also notice with this URL is the “link.edgepilot.com” at the start. This is because of the SPAM filter we use and have setup with many of our clients. This is an additional feature of the SPAM filter which, in addition to filtering out potential SPAM emails will check all links in emails if they are clicked on prior to taking the user to the site. While this doesn’t mean you can get click happy, it does offer another layer of protection against phishing emails.
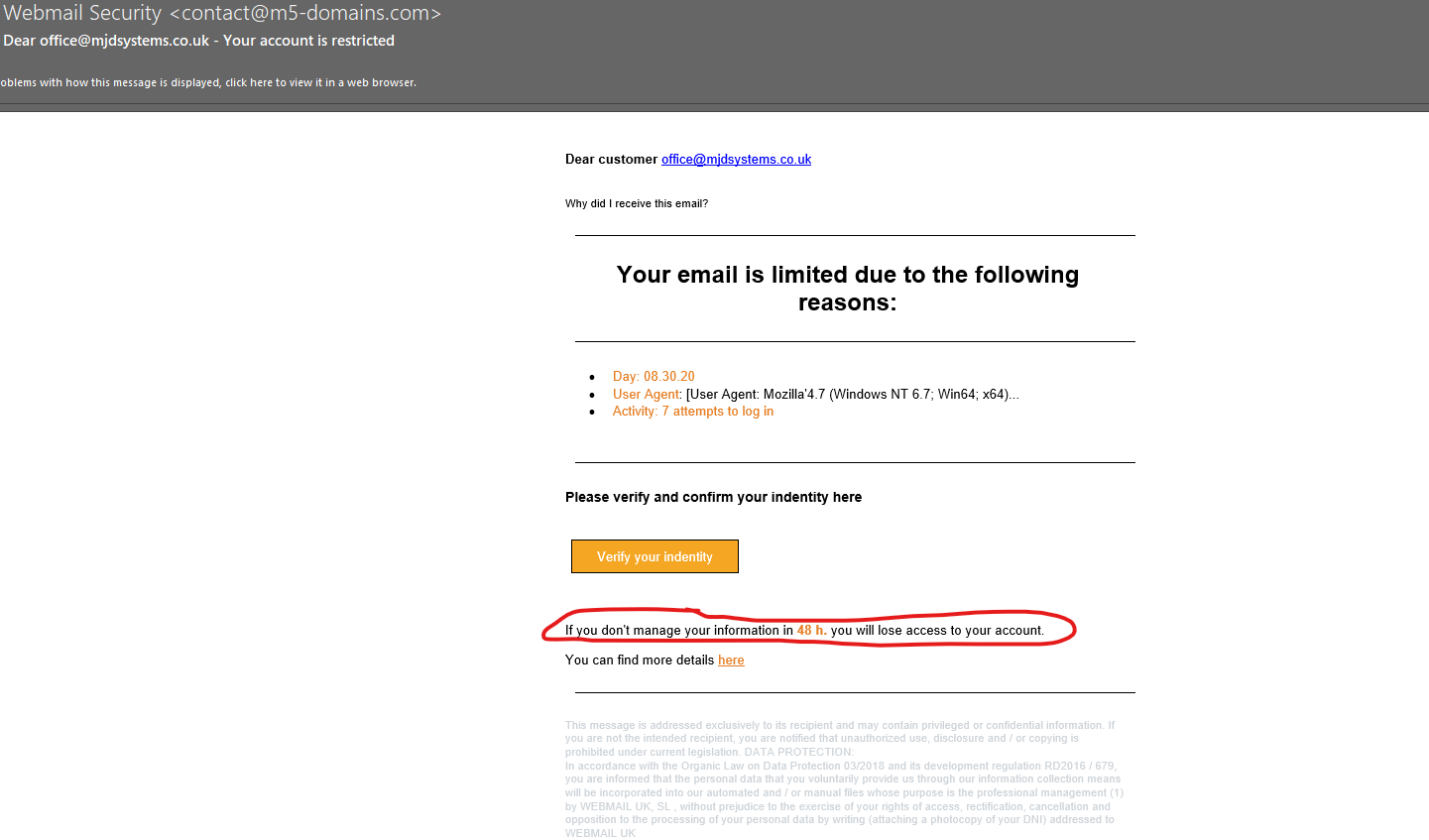
A time limit with a threat of losing access to your account, is another pressuring tactic to get you to take the wrong action.
If you are worried that there is potential the issue may be genuine, raise it with your IT department or your MSP/IT provider first. They will always be happy you checked with them, even if it turns out to be a phishing or spam email. The key is not to interact with the link or the sender of the email, any concerns ALWAYS contact your IT department or MSP first.
The final point to make is the small print.
First off, it’s in a lovely pale grey and small font to make it more difficult and off putting to read. But once you do read it, the references to laws and legislation do not make sense or aren’t relevant to any of our actual UK legislation. It also references a company, which hasn’t been mentioned previously, again providing us with further information that everything in this email doesn’t add up to a genuine warning from an email provider.
Hopefully, this will give you an initial check list of things to be mindful of when accessing emails and help you to identify emails that you need to be wary of and potentially ask your MSP for help to deal with. The team here at MJD have a variety of tools and packages which we can implement on your network to carry out on the job training for your organisation. If you’d be interested in developing a phishing email training programme for your organisation please don’t hesitate to get in touch with us.