With World Backup Day approaching on the 31st of March we wanted to highlight the importance of a backup and encourage everyone to run a backup on the 31st of March, especially if you have never done a backup before!
We have previously covered the topic of why a backup is important and tips on how to chose a suitable backup service for your circumstances which you can read here:
Why is a backup important?
Today lets highlight the top 3 reasons why you need to implement a backup system. Software as a Service (SaaS) apps do not back up your data, examples of these are Microsoft 365 and Google Mail. Now these services will assure you that THEY won’t lose your data, but what if YOU lost the data? In a recent report by Aberdeen Group (Read the report here) the top cause of data loss is human error. Consider your most important document to your business, how well could you cope if you lost it forever or at best had to wait 6 hours or more to retrieve it, could you survive?
Cyber attacks are not slowing down. In the first half of 2020, ransomware attacks increased by 715% exploiting the COVID-19 pandemic.
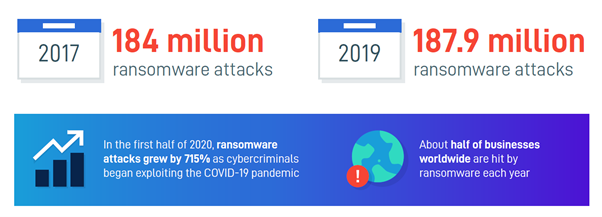
Also, there are at least 3.4 billion fake emails being sent every day around the world (Read the report here) all attempting to gather more information to determine email accounts to target their attacks on. Coupled with the fact Microsoft reported 480,000 accounts were compromised by “spraying” attacks. This is where the attackers run a common password such as “Winter2020!” against numerous accounts until they have success. If that number sounds big, compare it to the fact Microsoft stop 300 million fraudulent sign in attempts per day! Same as thinking about that business critical document, what would happen is you couldn’t access your email account for a day or more? We have a great blog article with advice on setting strong passwords here to help protect yourself from spraying attacks.
The evidence in the Small Business Reputation and the Cyber Risk report (Read the report here) shows that cyber security attacks are damaging SMEs, its not just the large multi national corporations that are targeted. 89% of SMEs reported that cyber breach ramifications are “huge and long-lasting”. 30% of SMEs surveyed reported lost of clients and 29% a reduction in their ability to win new business. So combined with losing current clients, you could also struggle to replace that business if you don’t protect your data. These costs far outweigh any capital and monthly costs of implementing a backup solution.

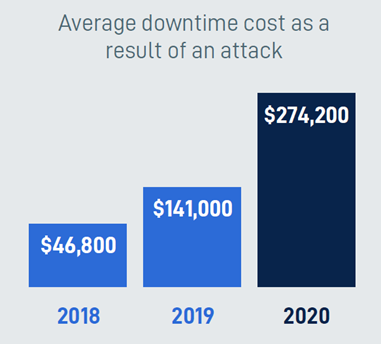
On a positive note, 4 in 5 small businesses with a comprehensive Business Continuity and Disaster Recovery (BCDR) recover from ransomware attacks within 24 hours. The average cost of downtime as a result of an attack for 2020 was $274,200 which has almost doubled since 2019.
If you have a comprehensive backup solution in place, such as a Datto system which is MJD’s chosen backup partner of choice, you can reduce that downtime cost considerably and not have to even consider paying the ransom to then also pay a MSP to decrypt the data as well. Not to mention the unproductive time of employees unable to perform your core business activities without access to your data.
If you are interested in implementing a Datto Backup System, or would like some advice on a backup solution please don’t hesitate to get in touch with the team here at MJD.









